Gitleaks digunakan untuk mendeteksi hard-coded password ataupun secret yang terdapat di repository. Baik di tambahkan secara sengaja maupaun tidak sengaja, Gitleaks ini sangat berguna bila ditambahkan di CI/CD sebagai bagian dari proses sebelum delivery.
Karena Gitleaks menggunakan regex untuk membaca secret yang ada, ada baiknya anda melakukan beberapa testing sebelum di implementasikan, karena regex sangat powerfull dan bisa salah dalam menangkap secret yang anda maksud.
Install
Download file binary dari rilis, contoh untuk linux
wget https://github.com/gitleaks/gitleaks/releases/download/v8.18.2/gitleaks_8.18.2_linux_x64.tar.gz
Ekstrak file yang baru di download
tar zxvf gitleaks_8.18.2_linux_x64.tar.gzPindahkan binary gitleak ke /usr/local/bin/
sudo mv gitleaks /usr/local/bin/
Cara Penggunaan
Config default gitleaks bisa di download dari https://raw.githubusercontent.com/gitleaks/gitleaks/master/config/gitleaks.toml, file ini bisa anda cek secara berkala.
Sebagai contoh mari kita download repository dummy-repo
git clone https://github.com/jaranguda/dummy-repo.git
struktur folder
../dummy-repo ├── dummy.crt ├── dummy.key ├── .gitleaks.toml ├── LICENSE ├── README.md └── secret.conf 1 directory, 6 files
Defaultnya gitleaks menggunakan file .gitleaks.toml yang ada di root folder repository tersebut, tetapi bila anda menggunakan file yang berbeda, bisa menambahkan --config dan lokasi gitleaks.toml. Contoh
# default gitleaks detect -v # gitleaks di folder yang berbeda gitleaks detect -v --config /repo/centralize-cicd/gitleaks/gitleaks.toml
Untuk menjalankan gitleaks dari mana saja, bisa menggunakan format berikut, contoh project ada di /home/project/dummy-repo.git
gitleaks detect --source="/home/project/dummy-repo.git" -v # gitleaks di folder yang berbeda gitleaks detect -v --source="/home/project/dummy-repo.git" --config /repo/centralize-cicd/gitleaks/gitleaks.toml
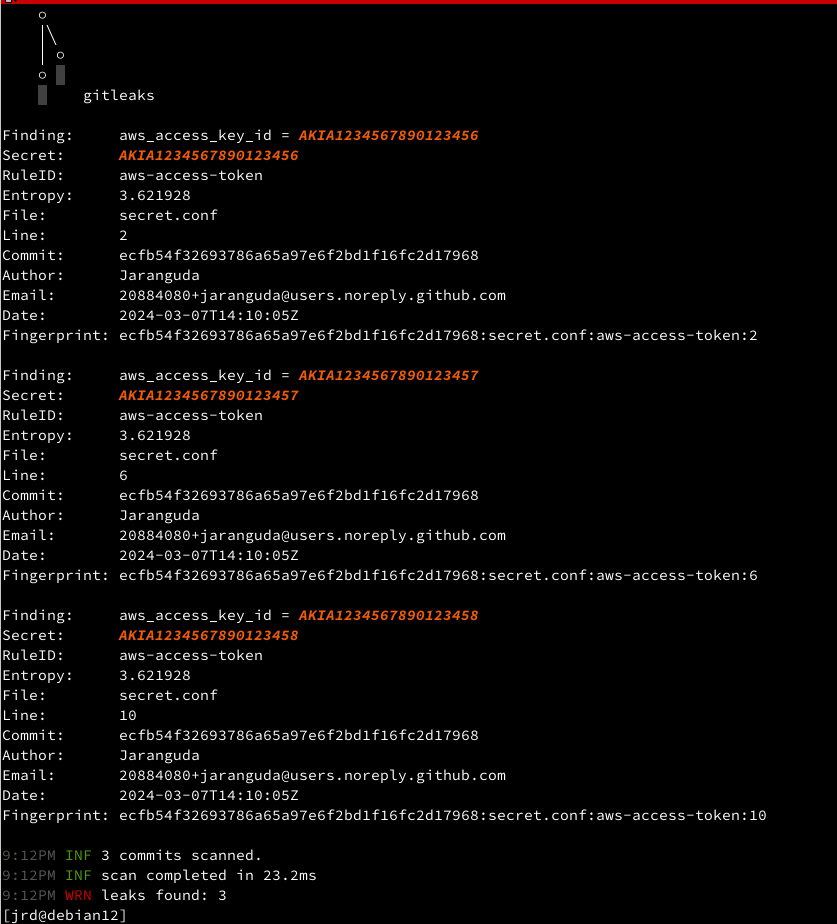
setelah di download, jalankan gitleaks
gitleaks detect -vFinding: aws_access_key_id = AKIA1234567890123456 Secret: AKIA1234567890123456 RuleID: aws-access-token Entropy: 3.621928 File: secret.conf Line: 2 Commit: ecfb54f32693786a65a97e6f2bd1f16fc2d17968 Author: Jaranguda Email: 20884080+jaranguda@users.noreply.github.com Date: 2024-03-07T14:10:05Z Fingerprint: ecfb54f32693786a65a97e6f2bd1f16fc2d17968:secret.conf:aws-access-token:2 Finding: aws_access_key_id = AKIA1234567890123457 Secret: AKIA1234567890123457 RuleID: aws-access-token Entropy: 3.621928 File: secret.conf Line: 6 Commit: ecfb54f32693786a65a97e6f2bd1f16fc2d17968 Author: Jaranguda Email: 20884080+jaranguda@users.noreply.github.com Date: 2024-03-07T14:10:05Z Fingerprint: ecfb54f32693786a65a97e6f2bd1f16fc2d17968:secret.conf:aws-access-token:6 Finding: aws_access_key_id = AKIA1234567890123458 Secret: AKIA1234567890123458 RuleID: aws-access-token Entropy: 3.621928 File: secret.conf Line: 10 Commit: ecfb54f32693786a65a97e6f2bd1f16fc2d17968 Author: Jaranguda Email: 20884080+jaranguda@users.noreply.github.com Date: 2024-03-07T14:10:05Z Fingerprint: ecfb54f32693786a65a97e6f2bd1f16fc2d17968:secret.conf:aws-access-token:10 Finding: -----BEGIN PRIVATE KEY----- MIIG/QIBADANBgkqhkiG9w0BAQEFAASCBucwggbjAgEAAoIBgQDViq9oprzvHbEN uOgJOZr... Secret: -----BEGIN PRIVATE KEY----- MIIG/QIBADANBgkqhkiG9w0BAQEFAASCBucwggbjAgEAAoIBgQDViq9oprzvHbEN uOgJOZr... RuleID: private-key Entropy: 6.031641 File: dummy.key Line: 1 Commit: dcb3bef76ad072198a65915cc1be0b162b38b8c8 Author: Jaranguda Email: 20884080+jaranguda@users.noreply.github.com Date: 2024-03-07T14:32:26Z Fingerprint: dcb3bef76ad072198a65915cc1be0b162b38b8c8:dummy.key:private-key:1
Membuat Allowlist
Dari output diatas gitleaks mendetiksi 4 secret yang di identifikasi sebagai aws-access-token. Bila ini bukan masalah, karena datanya dummy, bisa kita tambahkan ketiga aws_access_key_id diatas kedalam whitelist, caranya pada baris 27 dibawah allowlist, tambahkan
regexTarget = "line" regexes = [ '''aws_access_key_id = AKIA1234567890123456''', '''aws_access_key_id = AKIA1234567890123457''', '''aws_access_key_id = AKIA1234567890123458''', '''-----BEGIN PRIVATE KEY-----''', ]
Karena kita menggunakan regexTarget = "line", copy satu baris penuh dari code yang terdeteksi sebagai secret.
Jalankan kembali gitleaks, maka hasilnya bersih
$ gitleaks detect -v 9:37PM INF 5 commits scanned. 9:37PM INF scan completed in 22.7ms 9:37PM INF no leaks found
Membuat Rule Baru
Di repository dummy-repo yang tadi di download ada file dummy.crt yang berisi certificate request, sebagai contoh mari kita buat rule untuk mendeteksi ceritificate request tersebut
Copy file dibawah ini, lalu simpan ke dalam file .gitleaks.toml
[[rules]] id = "certificate-request" description = "Identified a Private Key, which may compromise cryptographic security and sensitive data encryption." regex = '''(?i)-----BEGIN[ A-Z0-9_-]{0,100}CERTIFICATE REQUEST( BLOCK)?-----[\s\S-]*REQUEST( BLOCK)?----''' keywords = [ "-----begin", ]
Rule tersebut merupakan perubahan dari rule private-key. Ada banyak rule yang bisa kita tambahkan, silahkan berkreasi sendiri dengan regex.
Command lengkap gitleaks
$ gitleaks --help Gitleaks scans code, past or present, for secrets Usage: gitleaks [command] Available Commands: completion generate the autocompletion script for the specified shell detect detect secrets in code help Help about any command protect protect secrets in code version display gitleaks version Flags: -b, --baseline-path string path to baseline with issues that can be ignored -c, --config string config file path order of precedence: 1. --config/-c 2. env var GITLEAKS_CONFIG 3. (--source/-s)/.gitleaks.toml If none of the three options are used, then gitleaks will use the default config --enable-rule gitleaks detect --enable-rule=atlassian-api-token --enable-rule=slack-access-token only enable specific rules by id, ex: gitleaks detect --enable-rule=atlassian-api-token --enable-rule=slack-access-token --exit-code int exit code when leaks have been encountered (default 1) --follow-symlinks scan files that are symlinks to other files -i, --gitleaks-ignore-path string path to .gitleaksignore file or folder containing one (default ".") -h, --help help for gitleaks --ignore-gitleaks-allow ignore gitleaks:allow comments -l, --log-level string log level (trace, debug, info, warn, error, fatal) (default "info") --log-opts string git log options --max-target-megabytes int files larger than this will be skipped --no-banner suppress banner --no-color turn off color for verbose output --redact uint[=100] redact secrets from logs and stdout. To redact only parts of the secret just apply a percent value from 0..100. For example --redact=20 (default 100%) -f, --report-format string output format (json, csv, junit, sarif) (default "json") -r, --report-path string report file -s, --source string path to source (default ".") -v, --verbose show verbose output from scan Use "gitleaks [command] --help" for more information about a command.